Instructions for Authors of Accepted Papers
Please revise your paper carefully according to the comments of the reviewers. Papers MUST BE formatted according to the guidelines of Springer Communications in Computer and Information Science (CCIS)Series. Failure to do so may result in the exclusion of your paper from the proceedings.
Please read the authors' instructions carefully before preparing your papers. Each paper is allowed to have 12 pages in the final camera-ready copy. At least one full paying author of each accepted paper must register for the conference before the deadline (January 05, 2014). Please note that this is a firm deadline to complete your registration - no further extensions will be given.
Before uploading your camera ready paper, please:
- Check that title and abstract in EDAS match your camera-ready paper exactly.
- Please use Title Case for the paper title, i.e. capitalising all main words.
- Compare all author names in EDAS with the author list in your paper. They MUST BE identical and in the same order.
This is very important because we will be using the information provided in EDAS to generate the final conference program and the table of contents for Springer Proceedings. The abstract and title should be readable stand-alone and not contain any references or unexplained acronyms. You are allowed to modify abstract and author list yourself. You cannot modify the title for the paper, please send a mail to snds2014.iiitmk@gmail.com if that is necessary and give a valid reason.
Important Steps
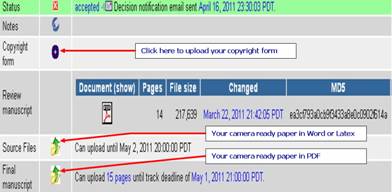
1. Upload your Camera ready paper (Final Manuscript) in PDF format on EDAS.
2. Upload the source files of your camera ready paper (WORD or Latex) on EDAS. All Latex files should be submitted as a single zipped file. DOCX files are not accepted.
The camera ready paper should be formatted according to the Springer template. This template can be downloaded here:
3. Submit the copyright form in PDF or image formats from the "Copyright" column in the My papers table or the individual paper page of EDAS.
Each contribution must be accompanied by a Springer copyright form. One author may sign on behalf of all of the authors of a particular paper. In this case, the author signs for and accepts responsibility for releasing the material on behalf of any and all co-authors.
Please make sure that you have entered the following details in the copyright form:
- Title of the Book/Volume/Conference: Second Intl. Conf. on Security in Computer Networks and Distributed Systems (SNDS'14)
- Volume Editors: G. M. Perez, S. M. Thampi, Ryan Ko and Lei Shu
- Title of Contribution: (Your Paper Title)
- Author(s) name(s):
- Corresponding Author's name, address, affiliation and e-mail:
- Signature of Corresponding Author:
4. Complete your registration.
The Registration Instructions and online Registration Form can be accessed via http://www.iiitmk.ac.in/snds/reg.html. In order to register, please click the link for 'Online Registration' and fill the particulars carefully. After making payment by your preferred mode, please scan and send the signed form to: snds2014.iiitmk@gmail.com .
Registration confirmation email will be sent to you by the conference Secretariat upon receipt of your payment and subject to realization of your payment in to the bank account. Please forward your queries on registration to snds2014.iiitmk@gmail.com
Call for Papers

|

|
SNDS invites submissions containing original ideas that are relevant to the scope of the conference. Like other conferences, SNDS requires that papers not be submitted simultaneously to any other conferences or publications; that submissions not be previously published in peer-reviewed conferences; and that accepted papers not be subsequently published elsewhere. Papers describing work that was previously published in a peer-reviewed workshop are allowed, if the authors clearly describe what significant new content has been included.
Authors should submit their papers online. We use EDAS system for submission of papers and review process. Unregistered authors should first create an account on EDAS to log on. Detailed usage instruction on EDAS can be found here. The manuscripts should be submitted in PDF format. All submitted papers will be subjected to a "similarity test" by EDAS paper similarity checker. Papers achieving a high similarity score will be examined and those that are deemed unacceptable will be rejected/withdrawn without a formal review.
Conference proceedings will be published by Springer in Communications in Computer and Information Science Series(CCIS), ISSN: 1865:0929. CCIS is abstracted/indexed in ISI Proceedings, Scopus, EI and DBLP. The contents will be included in the CCIS electronic book series hosted in the SpringerLink digital library.
Paper Length: 12 pages maximum
Springer Author Guidelines: PDF
Springer CCIS Manuscript Template: (Word format, LaTeX format)
All papers that conform to submission guidelines will be peer reviewed and evaluated based on originality, technical and/or research content/depth, correctness, relevance to conference, contributions, and readability. Acceptance of papers will be communicated to authors by email. All the accepted papers will be published in the conference proceedings. At least one full paying author of each accepted paper must register for the Conference before the indicated deadline.We welcome submissions for SNDS-2014's Technical Program in the following areas and not limited to:
Track 1: Cryptosystems, Algorithms, Primitives
Track 2: Security and Privacy in Networked Systems
Track 3: System and Network Security
|
Track 4: Multimedia Security
Track 5: Security Modeling, Experiments, Simulation, and Tools
Track 6: Other Security Topics
Best Paper AwardsAs evaluated by TPC Chairs and TPC Members, THREE papers will be given Best Paper Award for SNDS-2014 viz 1st, 2nd and 3rd respectively. The above committee will expect the presentation of the selected best papers during the conference before finalizing the list. The winners will be declared during the conference. |
Authors of selected outstanding papers will be invited to submit extended versions of their papers for consideration of publication in the following Journal(s):
-
International Journal of Trust Management in Computing and Communications (IJTMCC)
ISSN (Online): 2048-8386 - ISSN (Print): 2048-8378, Inder Science Publishers, Switzerland http://www.inderscience.com/IJTMCC
Key Dates
| Full Paper Submission Ends | |
| Acceptance Notification | December 18, 2013 |
| Final paper Deadline | January 5, 2014 |
| Author Registration Closes | January 7, 2014 |
| Conference | March 13 -14, 2014 |
